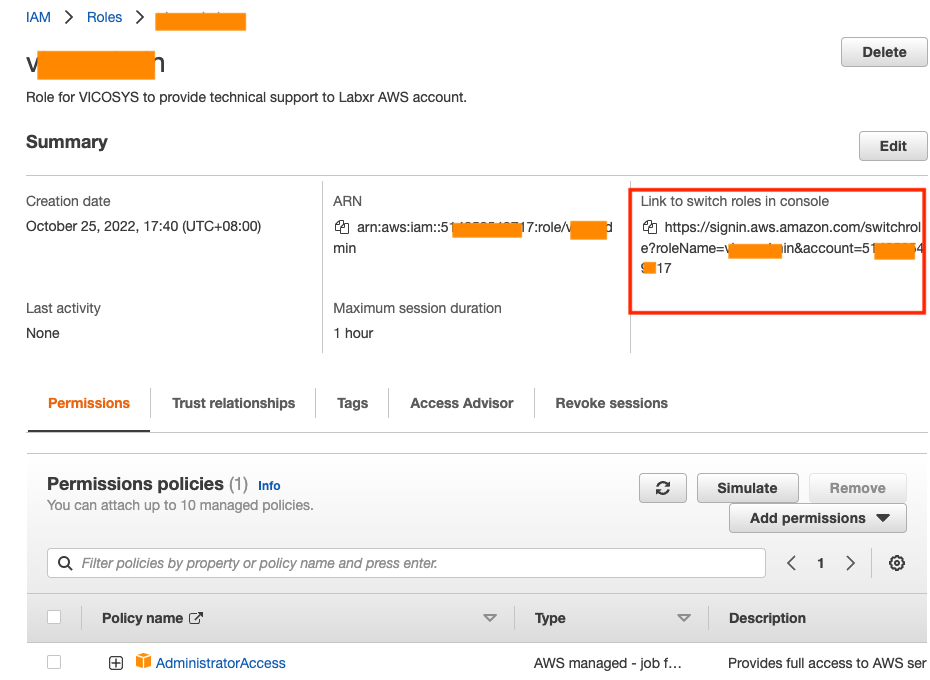
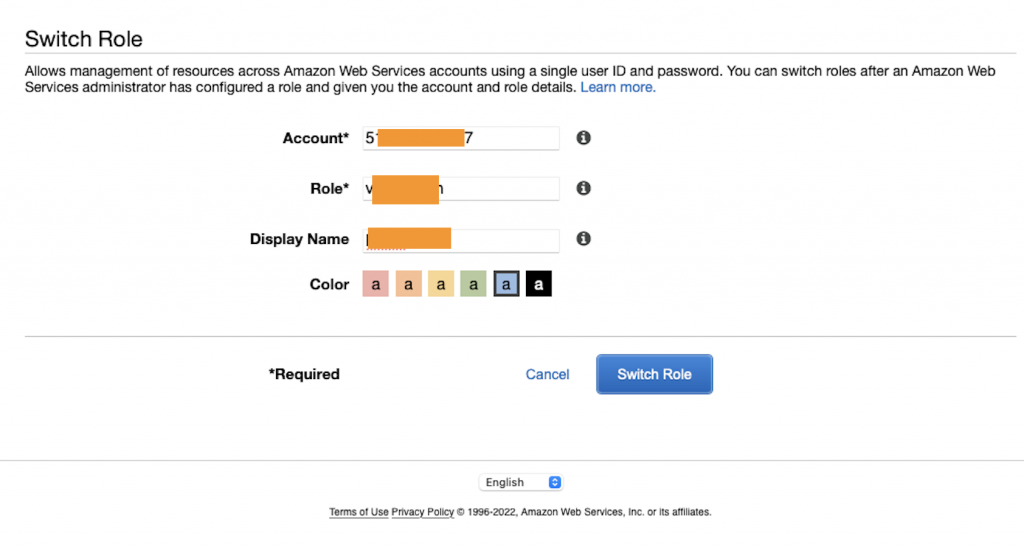
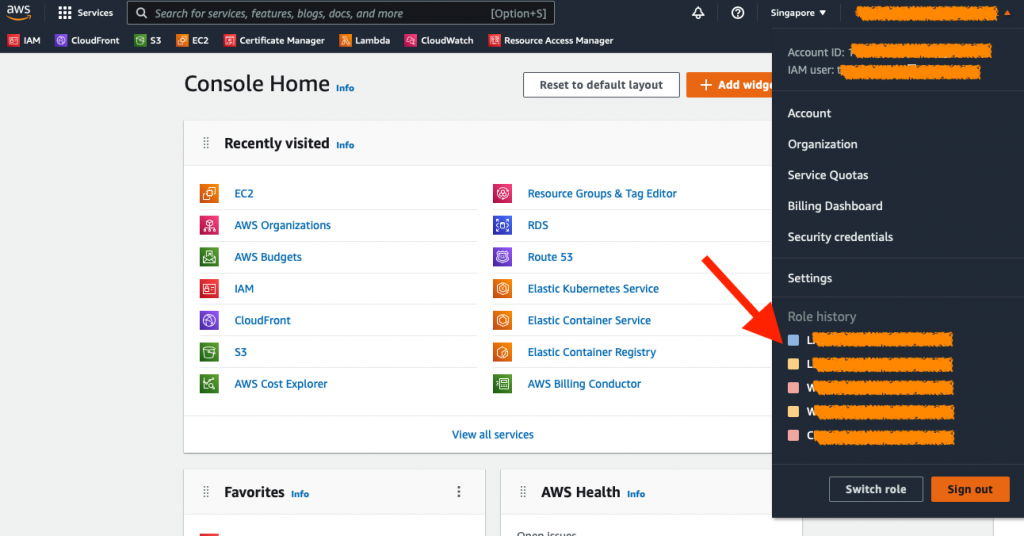
TCPDUMP
S = SYN: The synchronization flag is used when a connection is being established.
F = FIN: The finish flag is used to gracefully close a TCP connection.
R = RST: The reset flag is used to forcibly close a TCP connection.
P = PUSH: The push flag is used to ask the receiving end to pass this data to the application as soon as possible, rather than buffering it.
A = ACK: The acknowledgment flag is used to acknowledge receipt of packets.
U = URG: The urgent flag is used when certain data within a packet must be processed immediately.
E = ECE: The explicit congestion notification echo flag is used to signal network congestion.
C = CWR: The congestion window reduced flag is used to acknowledge the receipt of an ECE flag.
CISCO ASA
Quick Reference:
UIO = Outbound Connection
UIOB = Inbound Connection
Flags:
A – awaiting inside ACK to SYN,
a – awaiting outside ACK to SYN,
B – initial SYN from outside,
b – TCP state-bypass or nailed,
C – CTIQBE media,
D – DNS, d – dump,
E – outside back connection,
F – outside FIN,
f – inside FIN,
G – group,
g – MGCP,
H – H.323,
h – H.225.0,
I – inbound data,
i – incomplete,
J – GTP,
j – GTP data,
K – GTP t3-response
k – Skinny media,
M – SMTP data,
m – SIP media,
n – GUP
O – outbound data,
P – inside back connection,
p – Phone-proxy TFTP connection,
q – SQL*Net data,
R – outside acknowledged FIN,
R – UDP SUNRPC,
r – inside acknowledged FIN,
S – awaiting inside SYN,
s – awaiting outside SYN,
T – SIP,
t – SIP transient,
U – up,
V – VPN orphan,
W – WAAS,
X – inspected by service module